The rise of cryptojacking didn’t take those in the crypto-and-security worlds by surprise. In fact, the only surprising thing was perhaps the length of time it took malicious actors to use cryptojacking to mine for cryptocurrency.
As the cryptocurrency boom took hold at the end of 2017, so did a sudden surge in malicious cryptojacking incidents.
The phenomenal peaks of the cryptocurrency boom are long gone; cryptocurrency markets are somewhat stable, albeit still unpredictable. Has the decreased price correlated with a reduction in cryptojacking incidents? Do they relate at all? Here’s what you need to know.
What Is Cryptojacking?
Cryptojacking is the coverall term given to a malicious attack where unsuspecting users have their system hardware hijacked to mine cryptocurrency. The basic premise of a cryptojacking browser attack is:
- An unsuspecting user lands on a compromised webpage.
- The webpage has a small piece of JavaScript containing the cryptojacking code.
- The cryptojacking code hijacks the system CPU and puts it use mining cryptocurrency, usually Monero.
- In some cases, the JavaScript opens a minimized, hidden browser window. When the user leaves the site, the illicit crypto-mining continues.
- However, most cryptojacking attacks end when the website tab closes.
Cryptojacking isn’t just browser-based. There are several types of malware out there that will mine cryptocurrency after infecting your system. Most malware attempts to stay silent, but cryptojacking malware is more silent than most. The longer a cryptojacking malware variant can remain silent, the larger the potential reward for the attacker.
Cryptojacking, then, is theft. The unsuspecting users aren’t directly losing money, but they are losing system resources to power someone else’s financial gain. And while cryptojacking is malicious, it doesn’t leave any long-term damage to the target system, despite running the CPU at maximum or near-maximum capacity for a short amount of time.
Why Does Cryptojacking Use System Resources?
Cryptocurrency doesn’t grow on trees. No, it grows on servers, waiting for the right miners to come along and release it. Cryptojacking scripts primarily use the system CPU to do this.
Crypto-networks manage transactions through the blockchain. Each network transaction is added to a block. The block is distributed to a network of connected miners for verification. Each miner has a copy of the cryptocurrency specific blockchain and can validate and process transactions for that network.
When the new block arrives, the miner’s system processes complex equations to verify the block contents. On verification, the block adds to the blockchain, and the miners receive a pay-out reward for their efforts. In the case of Bitcoin, the reward is 12.5 BTC, shared between whoever contributes.
The key to crypto-mining success is speed and processing power. How quickly can your system verify the transactions within the block? Bitcoin mining is essentially useless for anyone not using specialized crypto-mining hardware. The sheer volume of mining power simply drowns out a tiny home desktop computer.
If Not Bitcoin, What Are They Mining?
Even as the Bitcoin price dropped from the heady $19,000+ mark back toward its current peaks and troughs, Bitcoin mining is inaccessible. Furthermore, Ethereum and ERC-20-based tokens use GPUs to mine cryptocurrencies. So just what are the cryptojackers attempting to mine?
For the most part, browser cryptojacking scripts and cryptojacking malware are mining Monero. The lightweight, privacy, and anonymity-focused cryptocurrency is easier to mine that Bitcoin and theoretically provides the crypto-mining thieves with protection after the fact. But not all. As you’ll read further down the article, several advanced cryptojacking threats mine Bitcoin.
But even though Monero is infinitely easier to mine than Bitcoin, it still requires raw computing power. Raw computing power requires investment in hardware. And let’s face it, if the mining thieves can steal the hardware with a tiny piece of JavaScript, why wouldn’t they try to maximize the profits?
JavaScript Cryptojacking
The first widespread cryptojacking JavaScript came from CoinHive, a company that wants to alter how we interact with the internet and the advertising profits that essentially underpin everything that takes place.
CoinHive’s vision was for authorized crypto-mining to replace advertising. Websites could still make an income based upon page views and the time spent on the site and users could avoid adverts without feeling awful for using an adblocker (and thus essentially robbing content creators of their fair dues).
Infamous content pirating and torrenting site, The Pirate Bay, was one of the first to experiment with the CoinHive model.
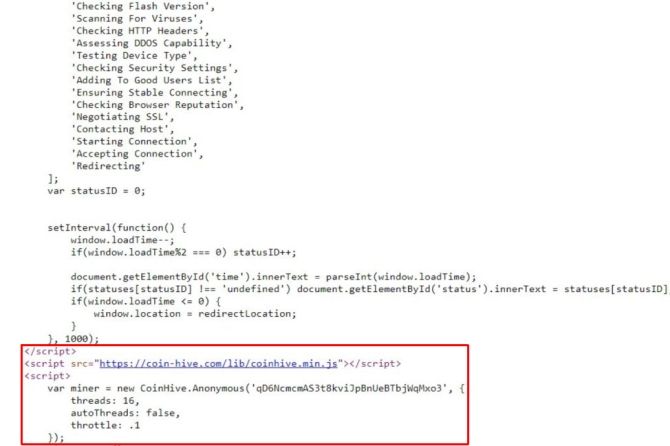
Unfortunately, it wasn’t long before malicious actors realized they could easily repurpose CoinHive’s mining script for more nefarious means. The original script has a CPU mining use percentage command. Originally set to 30% so users could happily continue using their browser, cryptojackers bumped this up to the full 100% on all cores, to maximize profits for the presumably short time most users linger on a malicious landing page.
To be fair to CoinHive, they realized what was going on and issued an update to their script. The newer version, known as AuthedMine, offers users the chance to opt-in to the crypto-mining process, regaining its peaceful-and-original purpose as an advertising alternative. That said, the opt-out is still opt-out. That is to say, website owners don’t have to use AuthedMine, and they’re under no obligation to inform you as to what is eating your CPU alive.
Cryptojacking Evolution
Cryptojacking is evolving. Like all profitable and largely risk-free cyber-attacks, malicious actors always want bigger gains for their investments and are prepared to shift cryptojacking forward to do so.
- In the early days of cryptojacking, one of the easiest methods to boost profits was to use a redirect loop. Unsuspecting victims are sent through a number of web pages before landing on one that has a crypto-mining script installed.
- Another already-mentioned technique is opening a new browser window that is minimized and hidden behind the taskbar. The minute browser window is hidden behind the system clock and is then “free” to run until the user notices something is afoot.
- Some browser extensions were found to conceal crypto-mining scripts without notifying the user. Some extensions were stolen from their developers, had the cryptojacking script injected, then were reuploaded or updated to the extension store. (In fact, Google swiftly banned all Chrome extensions abusing cryptojacking scripts.)
But that’s not all. Home users have relatively low power computers. Those running cryptojacking campaigns quickly realized there are bigger cryptojacking fish to fry: enterprises with powerful super-computers.
In February 2018, electric vehicle manufacturer Tesla announced they were the victims of a cryptojacking attack. RedLock Cloud Security Intelligence revealed that a vulnerable Kubernetes administration console exposed login credentials for a Tesla Amazon Web Service environment, and the hackers immediately turned the massive computing power to crypto-mining. British insurance provider, Aviva, and international digital security firm, Gemalto, also fell foul to the same cryptojacking vulnerability.
Other reports suggest that already vulnerable Internet of Thing devices are a prime target for cryptojacking, too. The Fortinet Threat Landscape Report [sign-up, PDF] found that 23 percent of its respondents were exposed to cryptojacking malware. IoT devices make an attractive, easy target due to their poor security, huge volume, and always-on status.
Cryptojacking Malware Explosion
However, other security leaks also contribute to the cryptojacking landscape. Remember the massive WannaCry ransomworm of 2017? WannaCry was the direct result of a liberated trove of previously unknown zero-day exploits that the NSA developed and amassed covertly. The Shadow Brokers, a hacking group with alleged ties to the Russian government, leaked numerous exploits, including EternalBlue (also styled ETERNALBLUE) which was crucial in spreading the WannaCry ransomworm at such a rapid pace.
Hackers around the world take notice when a tool causes such devastation (only saved by security researcher Marcus Hutchins, aka MalwareTech, who now faces a string of hacking allegations in the US). Combine EternalBlue with a malware payload that mines cryptocurrency and viola: suddenly we have WannaMine. WannaMine was first picked up by Panda Security and, like its ransomworm cousin, is extremely difficult to detect and block.
Nation-State Cryptojacking Malware Campaigns
But it isn’t just “regular” hackers putting cryptojacking malware to use. The North Korean state-sponsored hacking group, Lazarus (of Sony hack infamy), put a cryptojacking trojan to work against several high-profile banking institutions. Aside from the notable direct targeting of banking and financial organizations, the Lazarus “AppleJeus” attack almost uniquely targeted macOS systems, with a Linux exploit said to be in development.
Furthermore, since the presumably moderately successful AppleJeus attack, Lazarus is directly linked to the Ryuk cryptojacking malware which, at the time of writing, had stolen over $600,000. It isn’t just outlandish speculation; the Ryuk cryptojacking malware bears hallmarks of the Lazarus group Hermes malware variant (the same variant used to distract security services during the attempted $60 million heist on Taiwan’s Far Eastern International Bank). The Ryuk malware is interesting in that the targets appear to be hand-picked. That is to say, each ransom-note is different, makes a different demand, and so on. A personal service, almost.
Will Cryptojacking Get Worse?
Well, the rate of cryptojacking directly relates to the price of cryptocurrencies, as you might expect. The Fortinet Threat Landscape Report (linked above) illustrates this with the following chart:
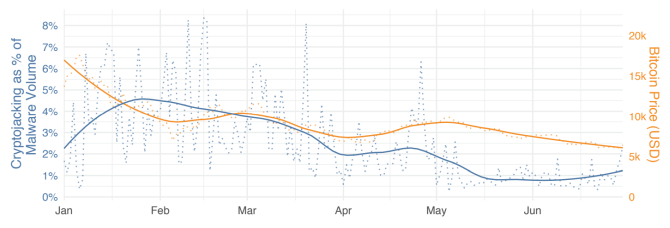
As the price of Bitcoin dropped, so did the incidents of cryptojacking.
Other reports don’t offer the same borderline positive information, though. The McAfee Labs Threats Report June 2018 [PDF] state that the “count of total coin miner malware rose by 629% in Q1, to more than 2.9 million samples.” The report elaborates further, confirming that in comparison with “well-established cybercrime activities such as data theft and ransomware, cryptojacking is simpler, more straightforward, and less risky.”
In that, you can see the appeal of browser-based cryptojacking and cryptojacking malware variants, especially in comparison to other financially motived attacks. Ransomware requires initial investment to spread the infection to enough victims, while victims still have the option to ignore the ransom and not pay, especially if the victim frequently takes system backups.
Cryptojacking isn’t going anywhere. And if cryptocurrency prices begin to rise in earnest, expect more malware to appear rapidly.
Read the full article: What Is Cryptojacking? How Websites Secretly Use Your CPU to Mine Cryptocurrency
from MakeUseOf https://ift.tt/2lNUmCU

![]() Owen Thomas / San Francisco Chronicle:
Owen Thomas / San Francisco Chronicle: