It’s been over a year since highly classified exploits built by the National Security Agency were stolen and published online.
One of the tools, dubbed EternalBlue, can covertly break into almost any Windows machine around the world. It didn’t take long for hackers to start using the exploits to run ransomware on thousands of computers, grinding hospitals and businesses to a halt. Two separate attacks in as many months used WannaCry and NotPetya ransomware, which spread like wildfire. Once a single computer in a network was infected, the malware would also target other devices on the network. The recovery was slow and cost companies hundreds of millions in damages.
Yet, more than a year since Microsoft released patches that slammed the backdoor shut, almost a million computers and networks are still unpatched and vulnerable to attack.
Although WannaCry infections have slowed, hackers are still using the publicly accessible NSA exploits to infect computers to mine cryptocurrency.
Nobody knows that better than one major Fortune 500 multinational, which was hit by a massive WannaMine cryptocurrency mining infection just days ago.
“Our customer is a very large corporation with multiple offices around the world,” said Amit Serper, who heads the security research team at Boston-based Cybereason.
“Once their first machine was hit the malware propagated to more than 1,000 machines in a day,” he said, without naming the company.
Cryptomining attacks have been around for a while. It’s more common for hackers to inject cryptocurrency mining code into vulnerable websites, but the payoffs are low. Some news sites are now installing their own mining code as an alternative to running ads.
But WannaMine works differently, Cybereason said in its post-mortem of the infection. By using those leaked NSA exploits to gain a single foothold into a network, the malware tries to infect any computer within. It’s persistent so the malware can survive a reboot. After it’s implanted, the malware uses the computer’s processor to mine cryptocurrency. On dozens, hundreds, or even thousands of computers, the malware can mine cryptocurrency far faster and more efficiently. Though it’s a drain on energy and computer resources, it can often go unnoticed.
After the malware spreads within the network, it modifies the power management settings to prevent the infected computer from going to sleep. Not only that, the malware tries to detect other cryptomining scripts running on the computer and terminates them — likely to squeeze every bit of energy out of the processor, maximizing its mining effort.
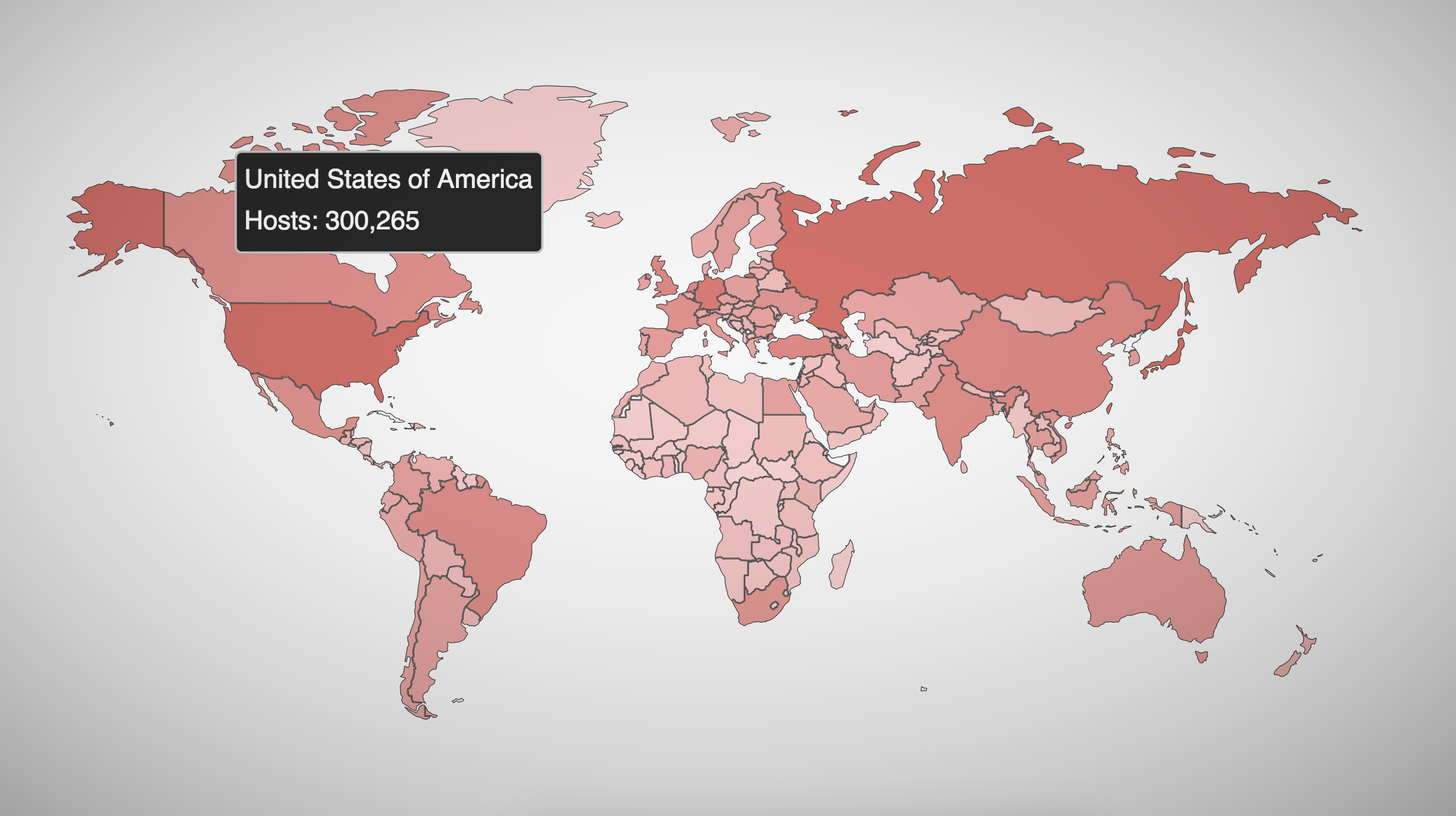
At least 300,000 computers or networks are still vulnerable to the NSA’s EternalBlue hacking tools.
Based on up-to-date statistics from Shodan, a search engine for open ports and databases, at least 919,000 servers are still vulnerable to EternalBlue, with some 300,000 machines in the US alone. And that’s just the tip of the iceberg — that figure can represent either individual vulnerable computers or a vulnerable network server capable of infecting hundreds or thousands more machines.
Cybereason said companies are still severely impacted because their systems aren’t protected.
“There’s no reason why these exploits should remain unpatched,” the blog post said. “Organizations need to install security patches and update machines.”
If not ransomware yesterday, it’s cryptomining malware today. Given how versatile the EternalBlue exploit is, tomorrow it could be something far worse — like data theft or destruction.
In other words: if you haven’t patched already, what are you waiting for?
from TechCrunch https://ift.tt/2OoJ303

No comments:
Post a Comment