Europol and the U.S. Justice Department, with help from six other countries, have disrupted and dismantled the GozNym malware, which they say stole more than $100 million from bank accounts since it first emerged.
In a press conference in The Hague, prosecutors said 10 defendants in five countries are accused of using the malware to steal money from more than 41,000 victims, mostly businesses and financial institutions.
Five defendants were arrested in Moldova, Bulgaria, Ukraine and Russia. The leader of the criminal network and his technical assistant are being prosecuted in Georgia.
The remaining five defendants, all Russian nationals, remain on the run and are wanted by the FBI, said prosecutors.
All were charged with conspiracy to commit computer fraud, conspiracy to commit wire and bank fraud, and conspiracy to commit money laundering. An eleventh member of the conspiracy, Krasimir Nikolov, was previously charged and extradited to the U.S. in 2016 and pleaded guilty in April in his role in the GozNym malware network.
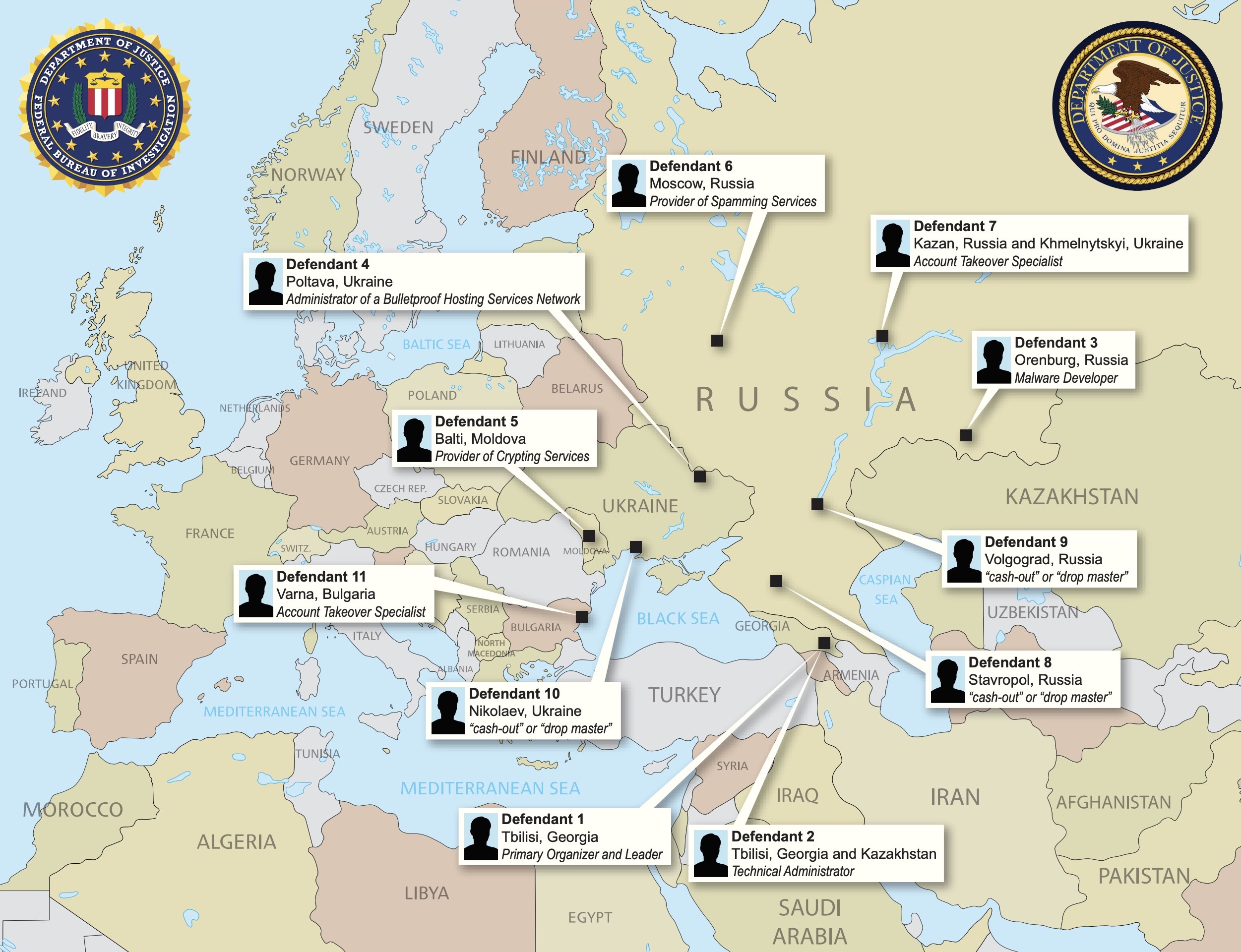
The names, roles and locations of the indicted suspects. (Image: Justice Department/supplied)
The takedown was described as an “unprecedented international effort” by Scott Brady, U.S. attorney for Western Philadelphia — where a grand jury indicted the defendants — at the press conference announcing the charges.
GozNym is a powerful banking malware that spread across the U.S., Canada, Germany and Poland. The malware was developed from two existing malware families, both of which had their source code leaked years earlier: Nymaim, a two-stage malware dropper that infects computers through exploit kits from malicious links or emails; and Gozi, a web injection module used to hook into the web browser, allowing the attacker to steal login credentials and passwords.
The banking malware hit dozens of banks and credit unions since it first emerged in 2016.
Described as malware “as a service,” the leader of the network allegedly obtained the code for the two malware families and built GozNym, then recruited accomplices and advertised the new malware on Russian speaking forums. The malware used encryption and other obfuscation techniques to avoid detection by antivirus tools. Then, spammers are said to have sent hundreds of thousands of phishing emails to infect staff at businesses and banks. After the malware infected its victim computers, the malware would steal the passwords control of bank accounts, which the criminals would later log in and cash out.
Prosecutors said the malware network was hosted and operated through a bulletproof service, a domain and web hosting known for lax attitudes towards cybercrime and favored by criminals. Europol said the 2016 takedown of Avalanche, an infrastructure platform used by hundreds of criminals to host and run their malware campaigns.
Although the victims were not named, the Justice Department said at least 11 U.S. businesses — including a church, two law firms, and a casino — fell victim to the GozNym criminals.
Read more:
The hacker group behind the Triton malware strikes again
A new cryptocurrency mining malware uses leaked NSA exploits to spread across enterprise networks
Researchers find a new malware-friendly hosting site after a spike in attacks
Shellbot malware evolves to spread and shuts down other cryptominers
TrickBot malware attacks are ramping up ahead of Tax Day
New malware pulls its instructions from code hidden in memes posted to Twitter
from TechCrunch https://tcrn.ch/2WKZ9FL

No comments:
Post a Comment