A popular GPS tracker — used as a panic alarm for elderly patients, to monitor kids, and track vehicles — contains security flaws, which security researchers say are so severe the device should be recalled.
The Chinese manufactured white-label location tracker, rebranded and sold by over a dozen companies — including Pebbell by HoIP Telecom, OwnFone Footprint, and SureSafeGo — uses a SIM card to connect to the 2G/GPRS cell network. Although none of the devices have internet connectivity and won’t be found on exposed device database sites like Shodan, they can still be remotely accessed and controlled by SMS.
Researchers at U.K. cybersecurity firm Fidus Information Security say the device can be tricked into turning over its real-time location simply by anyone sending it a text message with a keyword. Through another command, anyone can call the device and remotely listen in to its in-built microphone without alerting anyone.
Another command can remotely kill the cell signal altogether, rendering the device effectively useless.
Although the device can be protected with a PIN, it’s not enabled by default. Worse, the researchers found the device can be remotely reset without needing a PIN — opening up the device to further commands.
“This device is marketed at keeping the most vulnerable safe and yet anybody can locate and listen into thousands of people’s lives without their knowledge,” said Fidus’ Andrew Mabbitt, who wrote up the team’s findings. “This day and age, everything is connected one way or another and we seem to be leaving security behind; this isn’t going to end well.”
An attacker only requires the phone number of the device, Mabbitt told TechCrunch. His team showed it was easy to extrapolate hundreds of working phone numbers connected to vulnerable devices based off a single known device. “We made the assumption that these numbers were purchased in a batch,” said the team’s write-up.
The team bought a device and allowed TechCrunch to verify their findings. With a single command, we got a text message back in seconds with the precise co-ordinates of its location. We could also pull other information from the device, including its IMEI number and battery level.
The phone call trick, which Mabbitt called a “glorified wiretap,” also worked.
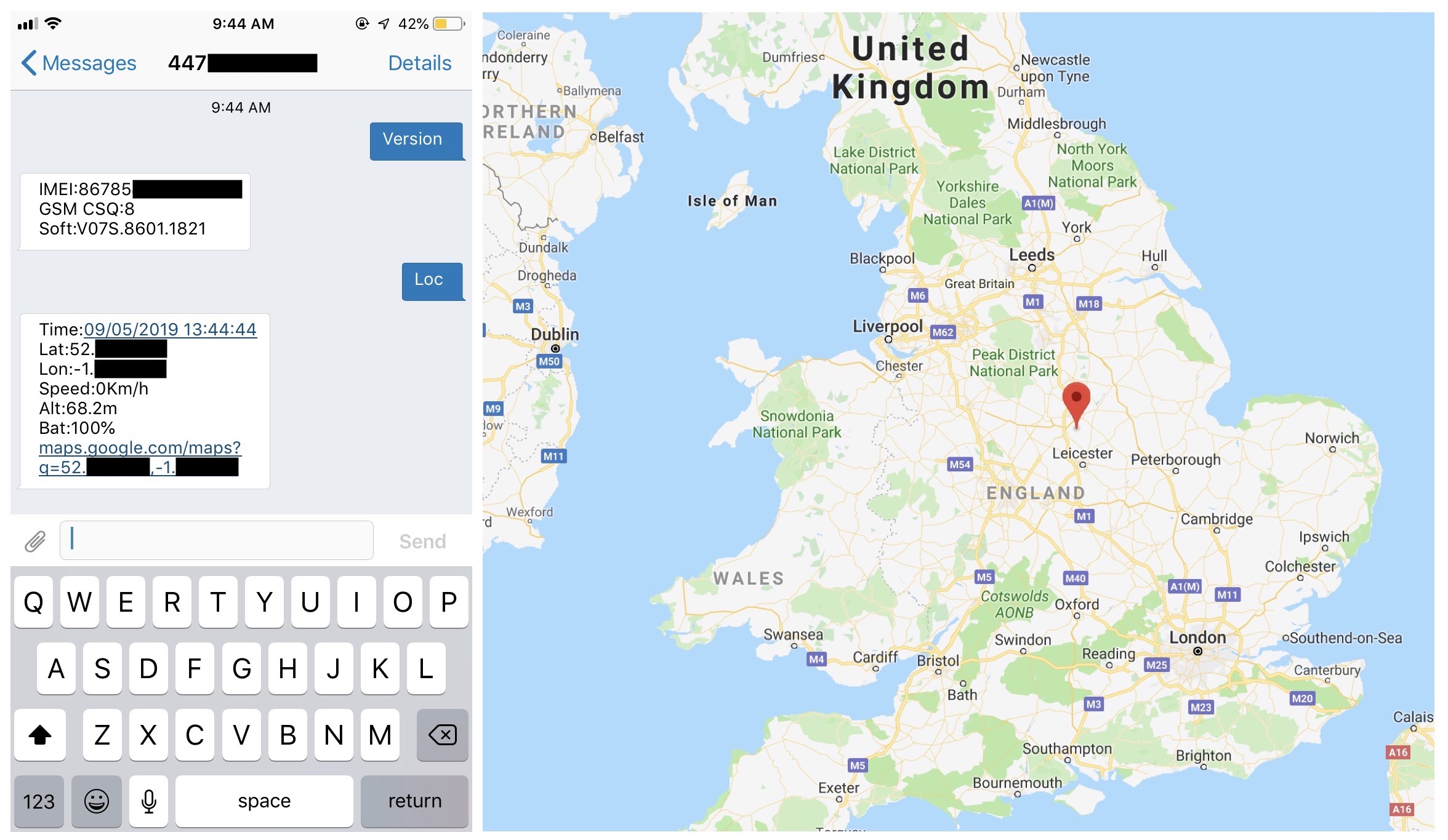
One text message to a vulnerable device, bought by the security researchers, allowed us to remotely grab its real-time coordinates. The geolocation was precise to a few meters. (Image: TechCrunch)
There are an estimated 10,000 devices are in the U.K. — and thousands more around the world. The team told several of the device makers of the flaws, but Mabbitt said there’s no way to fix the vulnerabilities without recalling every device.
“Fixing this broken security would be trivial,” said the team. “All they needed to do was print a unique code on each pendant and require that to be used to change configurations. The location and call functions could be locked down to calls and texts only from those numbers previously programmed in as emergency contacts.”
The U.K. just last week announced a proposed new cybersecurity law that would require connected devices to be sold with a unique password, and not a default.
None of the device sellers we contacted responded to a request for comment.
Read more:
- An unsecured SMS spam operation doxxed its owners
- Samsung spilled SmartThings app source code and secret keys
- Security lapse exposed a Chinese smart city surveillance system
- A leaky database of SMS text messages exposed password resets and two-factor codes
- Chipotle customers are saying their accounts have been hacked
- We found a massive spam operation — and sunk its server
- Dow Jones’ watchlist of 2.4 million high-risk individuals has leaked
- Robocaller firm Stratics Networks exposed millions of call recordings
- Massive mortgage and loan data leak gets worse as original documents also exposed
from TechCrunch https://tcrn.ch/307SQxY

No comments:
Post a Comment